Connecting Bonita Cloud to your VPN
To connect Bonita Cloud to your private network, you can request for a site-to-site VPN connection.
It will allow Bonita environments to interact with your internal information systems not exposed on the Internet (LDAP server…).
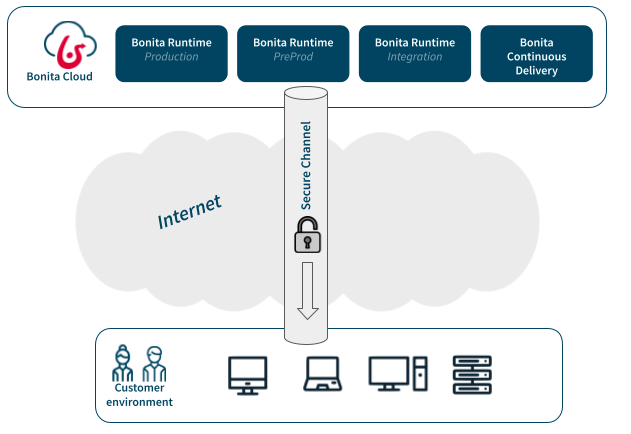
Bonita Cloud supports Internet Protocol security (IPsec) VPN connections.
Failover
Two tunnels between VPN gateways can be configured to guarantee the secure connection between your network and Bonita Cloud.
Traffic from Internet to Bonita Cloud
To ensure a versatile connectivity from anywhere, Bonita Cloud will continue to allow connections from public internet. This is done through a secured HTTPS link (supporting TLS 1.3).
Traffic from Bonita Cloud to Internet
It’s still autorized to let your processes interact with public resources.
Traffic from Bonita Cloud to customer’s private network
Bonita Cloud will be able to securely connect to your internal resources which are not exposed on the Internet.
| This private communication is still subject to the firewall rules you have in place on your own equipments. |
Traffic from customer’s private network to Bonita Cloud
Your Bonita Cloud environments are not accessible from the VPN.
Impacts on the availability
Bonitasoft will guarantee the availability of the VPN gateway on the Bonita Cloud side. However, Bonitasoft is not responsible for issues on the customer side of the VPN (unreachable data for Bonita or impossibility for the customer’s user to connect to the VPN).
Requesting a VPN Integration
To request a VPN connection with Bonita Cloud, create a new case on the Customer Service Center. Select Professional Services as the type of request and make sure to provide the following information in your case:
-
VPN gateway type
-
Gateway public IP address
-
Encryption algorithms (AES-128, AES-256)
-
Integrity algorithms (SHA2-256, SHA2-384, SHA2-512)
-
IPsec protocols (IKEv1, IKEv2)
-
Authentication modes (pre-shared key/digital signature)
-
Diffie-Hellman groups (2, 14, 15, 16, 17, 18, 19, 20, 21, 22, 23, 24)
-
Addressing plan/Netmask